Crypto Wallet Security: The Importance of Private Endpoints in Safeguarding Your Cryptocurrency
Cryptocurrency and frequent use of wallets has taken the web3 world by storm, and with its increasing presence in our day-to-day interactions, the need for secure storage of these digital assets has become more significant than ever.
More specifically, the vulnerability of blockchain endpoints is an important security concern in blockchain. It is a crucial point of entry for users as it provides them with the means to engage with the blockchain’s decentralized infrastructure and perform a variety of functions such as initiating transactions, verifying data, and accessing smart contracts. The endpoint acts as an interface between the user’s device and the underlying blockchain network, enabling users to communicate with the network in a secure and efficient manner. Making sure of the secureness of these endpoints is vital for taking proper wallet security measures.
Being a blockchain customer, one has to learn the legislative consequences and endpoint security risks associated with this technology.
Securing your Crypto Wallet and Transactions through RPC Endpoints with OMNIA
When you trade on centralized exchanges, the transactions occur instantaneously. When it is a decentralized exchange however, the transaction has to be broadcasted to the network. Between the moment you sign off on the interaction, to the pending stage, to its completion, the user and the wallet in use is vulnerable.
During these transactions, various malicious activities can occur. For example, when a pending transaction is being broadcasted to the public, frontrunning, sometimes referred as a savage attack, can occur. It is one of the biggest issues to watch out for. In the case where secure OMNIA endpoints are not used, there is technically no privacy of the intention or the transaction the user is conducting, and you are prone to be at risk. But, if you opt for frontrunning protection through OMNIA, your transactions will be a “private transaction” which will bypass the public mempool. The private mempool operator ensures that there is a private secure channel that doesn’t leak any information, which means that bots can no longer influence the route of the transaction.
What are RPC Endpoints?
We need to initially understand what RPC endpoints are to correctly define its importance in implementing the right wallet security measures. RPC nodes act as intermediaries between blockchains and dApps, enabling seamless interaction between the two. Default RPC node providers on Web3 wallets facilitate easy access to web3 applications, but they often suffer from issues such as sluggish network speeds, inaccurate blockchain data, and unreliability. To overcome these issues, it is recommended to set up a private RPC endpoint, which is a personal endpoint that is not accessible to the public.
How can you Protect your Crypto Wallet from Vulnerabilities?
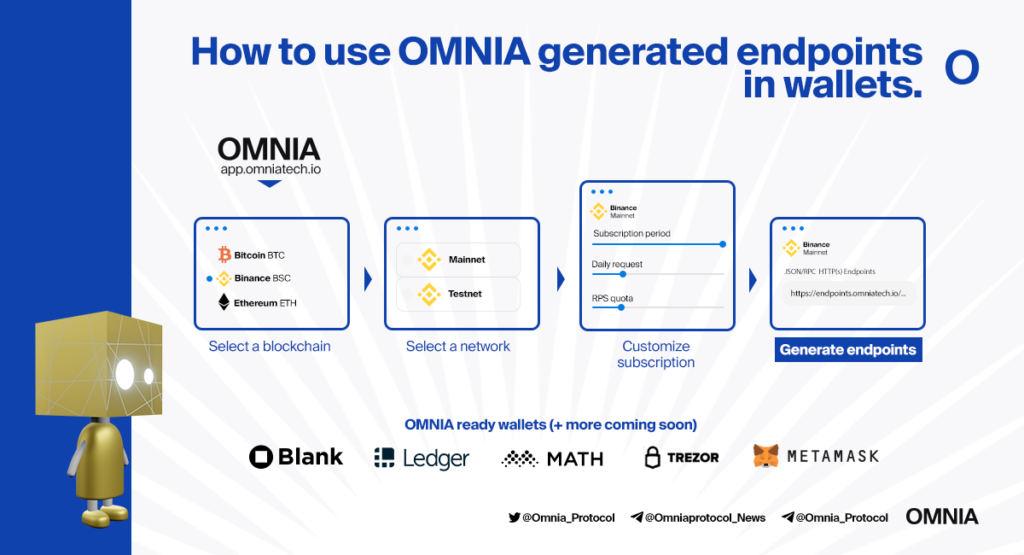
When a user buys a subscription through the application, an OMNIA endpoint will be generated, which is essentially a connection with the blockchain. In a regular, non-blockchain world, this can be simplified as a connection to a server.
The endpoint will go through a load balancer, and distribute requests through a resource pool which is made up of all active nodes in the system. The importance of wallet security is related to the fact that as a regular user, you’re most likely oblivious to the back end occurings, even though data related to the activities you conduct can easily be leaked. However, with an OMNIA generated endpoint, the data is protected at the network level and within private mempools.
- The RPC URL has a unique identifier that is configured via OMNIA.
- It is more frictionless if you choose to deploy OMNIA endpoints, as they are the ones taking care of security and privacy through the simple application interface.
- The wallets actually gain an advantage over unprotected users as all transactions are protected from malicious activities.
- The Smart Guard Check also allows an extra layer of security, in partnership with Chain Analysis, as the system also identifies transactions related to mixers, drug selling on the market, channel trafficking issues and so on, and gives details as to what the exposure is and ultimately cancels the transaction if it deems it to be insecure.
5 Easy Steps to Add a Secure RPC Endpoint to your Crypto Wallet
- Copy the JSON RPC Endpoint URL via OMNIA’s generated secure endpoints.
- Open your wallet, such as Metamask, and add a network.
- Input your preferred network name.
- Paste the RPC URL address.
- Input Chain ID and Currency symbol.
- Save and enjoy a secure endpoint for all your transactions.
Take a look at this video for detailed steps, and a guided instruction with visuals for instructions on setting up your first endpoint with OMNIA!
Current Threats to Crypto Wallet Security
Crypto wallets are not immune to attacks, and various threats exist that can compromise the security of your crypto assets if you don’t take the necessary steps, such as safeguarding your endpoints. The first section of the blog mainly consisted of OMNIA’s solution to safeguarding your crypto wallet, the following section will discuss the possible threats to watch out for.
- Web/browser based wallets can be vulnerable to malware attacks because browsers are a common target for exploits and attacks that can give attackers access to your device’s memory. Moreover, cybercriminals can launch phishing attempts, tricking users into entering sensitive information such as login credentials, private keys, or transaction details into malicious versions of transaction screens such as “import account” or “send transaction.” In some cases, attackers can replace the content of the clipboard with their wallet address to steal funds.
- Exchange/Custodial wallets face a different set of risks. Since these wallets are controlled entirely by a third party, users are entrusting their funds and personal data to an external entity. The organization that manages the funds must implement enterprise-wide security measures such as key management, application security, and data security to protect user information. However, users who rely on custodial services are also at risk of falling prey to phishing scams that can harvest login credentials, leaving their funds vulnerable to theft.
- “Experts warn of new phishing scam targeting cryptocurrency wallets”
- This article, published by CNBC in January 2022, reports on a new phishing scam that is targeting users of crypto wallets. Hackers are using social engineering tactics to trick users into revealing their private keys or login credentials, which can then be used to steal their crypto assets.
- “Ledger wallet users report more phishing attacks following data breach”
- This article, published by Coin Telegraph in July 2021, reports on the fallout from a data breach at the crypto wallet company Ledger. Hackers were able to access the personal information of Ledger wallet users, which has led to an increase in phishing attacks targeting these users.
- Social engineering attacks are the most common form of cyberattack, and identifying suspicious indicators is key to prevention. Examples of indicators include poor grammar and unusual formatting in phishing emails, irregular URLs, typos, or design inconsistencies in suspicious websites, and any email or offer that seems too good to be true or demands immediate action. Countermeasures include antivirus and anti-malware software, multi factor authentication, updating operating systems, keeping strong passwords, limiting the use of personal information, and avoiding unfamiliar USB sticks or leaving devices unattended.
- Wallets that can be stored on mobile devices, such as crypto wallet apps, are vulnerable to mobile security risks. These apps may not be able to determine if a device is secure or has been tampered with. Mobile malware can exploit these vulnerabilities to access sensitive information such as user credentials, private keys, and seed phrases stored in the app’s memory. Additionally, if the wallet app doesn’t require a device-level passcode, attackers can easily unlock the device and gain access to key storage and keychains.
All of these risks are an indication that proper security measures must be taken by the user to ensure that vulnerabilities are reduced, and your money and transactions can be safe. OMNIA has developed an Untraceable blockchain nodes infrastructure in order to mitigate these risks and allow privacy-first access to blockchains.
Take a look at this article for additional information regarding an emphasis on the important features of secure wallets.
Maintaining Crypto Wallet Security with OMNIA
Understanding the need for extra security layers, and a quick and easy solution to protecting your wallets, OMNIA has come up with a service in which users can create secure endpoints for their wallet that provide a private and secure connection to the blockchain. The process involves redirecting traffic through advanced mixnets and privacy relayers to safeguard against malicious attacks.
Omnia provides you a secure RPC endpoint with high availability to access the blockchain without being traced or monitored.
Overall, maintaining strong wallet security is essential for protecting your assets, building trust and credibility, and ensuring compliance with regulations.