Axie Infinity Hack is an Industry Problem
The Ronin Validator security breach by the North Korean-based Lazarus hacker group and APT38 will go down in DeFi history as one of the largest in terms of total value stolen.
According to the team at Ronin, the security breach resulted in the loss of 173,600 Ethereum and 25.5 million USD Coin. This amount in digital assets translates to a 615 million dollars loss using an Ethereum value of $3,400 at the time of the hack in late March 2022. To note is that $400 million of the funds lost belonged to the Axie Infinity gaming metaverse players.
Lack of Node Decentralization is an Industry Problem
At the time of the exploit, the Sky Mavis Ronin chain consisted of 9 validator nodes, with five out of the nine validator signatures needed to execute a deposit or withdrawal event. The attackers managed to get a hold of hacked private keys to five of these validator nodes: four belonging to Ronin validators and a third-party validator run by Axie DAO. In essence, the hackers gained over 50% control of the Ronin network with one swift move.
Theoretically, the decentralized design of validator nodes should have prevented the Ronin Network attackers from pulling off the heist. But the hackers found a backdoor through a gas-free RPC (Remote Procedure Call) node, which was used to get the signature for the Axie DAO validator. (An RPC node is a straightforward API that allows developers to communicate to a server to execute code remotely.)
Consequently, the Lazarus hacker group was able to get the signature from the Axie DAO validator through the gas-free RPC, thus kickstarting the withdrawal of the earlier mentioned Ethereum and USDC.
The ease at which the five validator nodes were compromised brings to light inherent decentralization weaknesses found in bridge protocols and DeFi platforms that rely on proof-of-stake consensus mechanisms such as the one by the Ronin Network. To increase decentralization and further mitigate another potential attack, the team at Ronin has increased the number of nodes needed to start a withdrawal event from the original five to eight.
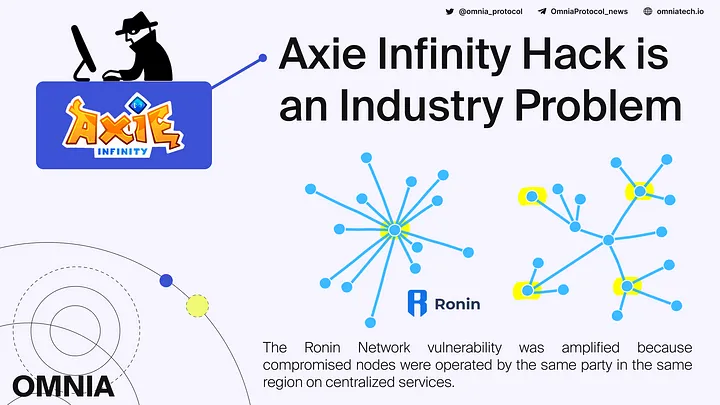
The Ronin Network vulnerability was further amplified by the fact that the compromised nodes were operated by the same party in the same region, and the nodes were run on centralized services. Having five of the nine validator nodes as a threshold to kickstart a withdrawal event was okay, provided the validators followed node decentralization best practices.
True node decentralization is a question of ‘spreading out’ the nodes in terms of geographic location, operator diversity (who in the community is running the node), and data center diversity (which cloud service provider is contracted to run the node, e.g., AWS, ).
Prevention Techniques For Hacks
1. Node Decentralization Reduces Hacks and Single Points of Failure
a. Geographic Diversity
As highlighted above, the setting up of validator nodes should prioritize diversifying geographic locations. Too many nodes in one region or country can bring operational complexities if the stated region is the victim of political laws that ban cryptocurrency operations such as mining or digital assets as a form of payment. Wars also do happen abruptly, disrupting internet and power services.
Recently we have seen the hash rate of the Bitcoin network drop significantly as a result of China banning Bitcoin mining and crypto trading within its territories. Miners who had set up shop in China due to cheap electricity were forced to ship their miners to Bitcoin-friendly countries such as the United States and Kazakhstan. However, those who shipped their miners to Kazakhstan were faced with internet outages in January as part of government measures to quell civilian protests ignited by a rise in fuel prices.
b. Operator Node Diversity
Concerning operator diversity, one entity running multiple nodes creates a very concerning single point of failure. An affordable means to run network nodes needs to be devised to increase community participation and network security. A few die-hard fans have done so; however, hurdles still exist, such as awareness of the technology, the know-how of node setup, and financial costs.
OMNIA Protocol offers such a solution as it incentivizes anyone to host a node or even run it in the cloud using a no-code/low-code approach. OMNIA currently supports five networks: Bitcoin, Ethereum, Binance Smart Chain (BSC), Polygon, and Avalanche. Existing nodes of these five networks will be able to join OMNIA’s resource pool without upgrading the hardware equipment; minimal requirements do exist, though.
Consequently, initial costs to run OMNIA’s supported nodes with personal hardware will be near zero. Due to increased requests per second and high network throughput, node owners running on cloud services such as AWS will have to pay more for the service. Alternatively, one can take advantage of OMNIA’s no-code/low-code approach and benefit from cloud automation for node deployment within cloud infrastructure institutional partners, thus being able to optimize the costs.
Running an OMNIA node or privacy relayer does not require extensive technical knowledge, further boosting participation amongst the crypto and blockchain community. Those with an existing node running a supported blockchain need only add it to OMNIA through a simple web interface that requires the URL/IP of the node, credentials to access it (if configured), an availability offer, and the performance quota — the latter is automatically computed by a benchmarking service.
In addition, OMNIA will have incentives for its community members who wish to run nodes or privacy relayers, thus increasing its network’s chances of participation and decentralization.
c. Data Center Diversity
Finally, true decentralization is a question of diversifying data centers. OMNIA’s co-founder, Alex Lupascu, had highlighted the issue of centralization on Ethereum by pointing out that Amazon Web Services handles nearly a quarter of Ethereum nodes. Microsoft Azure, Alibaba Cloud, Google Cloud Platform, DigitalOcean, and Hetzner also host many Ethereum Nodes. These cloud service providers are American-owned and based, causing an uneven distribution of Ethereum nodes.
Such centralization can cripple the Ethereum network, as was witnessed on December 8th, 2021, when Amazon Web Services went down for nearly half a day. The outage caused operational interruptions for the centralized exchanges of Binance, Coinbase, and KuCoin. Decentralized exchanges were also not immune to the AWS outage as dYdX could not process transactions during this period.
Therefore, diversifying cloud service providers is a possible way of mitigating potential blockchain outages and potential security breaches in the case of the Ronin Network.
2. Revoking and Reviewing Remote Access Privileges
Circling back to how DeFi hacks can be prevented, we investigate a critical component of the Ronin Network exploit: access to the RPC node.
The RPC node was available between November 2021 and December 2021, when the Axie DAO had allowed its parent company, Sky Mavis, to sign various transactions on its behalf. But, Axie DAO did not revoke Sky Mavis’ privileges once the need for remote access was no longer required.
The RPC node still being active past December 2021 was one of the reasons the Lazarus group hacked the Ronin Network. There is a possibility that the exploit could have been prevented or delayed if the remote access privileges had been revoked as soon as Sky Mavis had completed its task of signing transactions on behalf of Axie Infinity. A review of privileges should have identified the remote access as a potential risk and discontinued access immediately.
3. Bug Bounty Programs
Additionally, DeFi protocols such as Axie Infinity should consider constant reviews and audits of their code to prevent motivated attackers, such as the North Korean Lazarus group, from draining funds belonging to users who entrust their holdings to the developers of these platforms.
The use of bug bounty programs should be considered to boost the probabilities of finding critical bugs ahead of time. Bug bounties have proven to motivate ethical or white hat hackers to investigate and secure vulnerabilities before malicious hackers get a hold of them.
A practical example of a white hacker identifying a vulnerability was the $610 million heist on the Poly Network in June 2021. Although there was no initial bug bounty, the hacker stole the stated funds to call attention to a weakness. He then returned the stolen digital assets after the team at Poly Network offered him a $500k bounty and promised not to pursue legal charges.
Conclusion
Summing it up, the Ronin Network exploit that resulted in the $615 million loss of user funds in Ethereum and USDC was particularly alarming to the entire DeFi industry but has provided several learning opportunities to assist future networks and protocols in plugging the numerous potential vulnerabilities.
From a different perspective of optimism, the hack will probably prevent the loss of more funds to malicious actors such as the North Korean state-sponsored hacker groups that have devastated the DeFi realm in the last few years.
The DeFi industry is here to stay. Optimizing decentralization is part of its growing pains that will hopefully be achieved through time and as community members commit personal resources towards running nodes at various locations across the globe.


